Configuration Settings
The Structr application plattform has a variety of configuration settings that control properties of the application such as the database connections, mail configurations, services (such as ftp, cron jobs or ldap), various types of logging and oauth configurations. These setting can either be configured via a configuration file or via the configuration tool.
Changes to the configuration file requires a restart of Structr to become effective. In contrast, most setting changes made via the configuration tool become effective immediately. In particular, services may have to be (re)started via the respective tab in the interface. For this reason, and because of the available tooltips, the configuration interface is the recommended way of making changes to the Structr settings.
This section provides a comprehensive overview over the settings that can be configured in Structr. The settings in Structr are divided into the following broad categories:
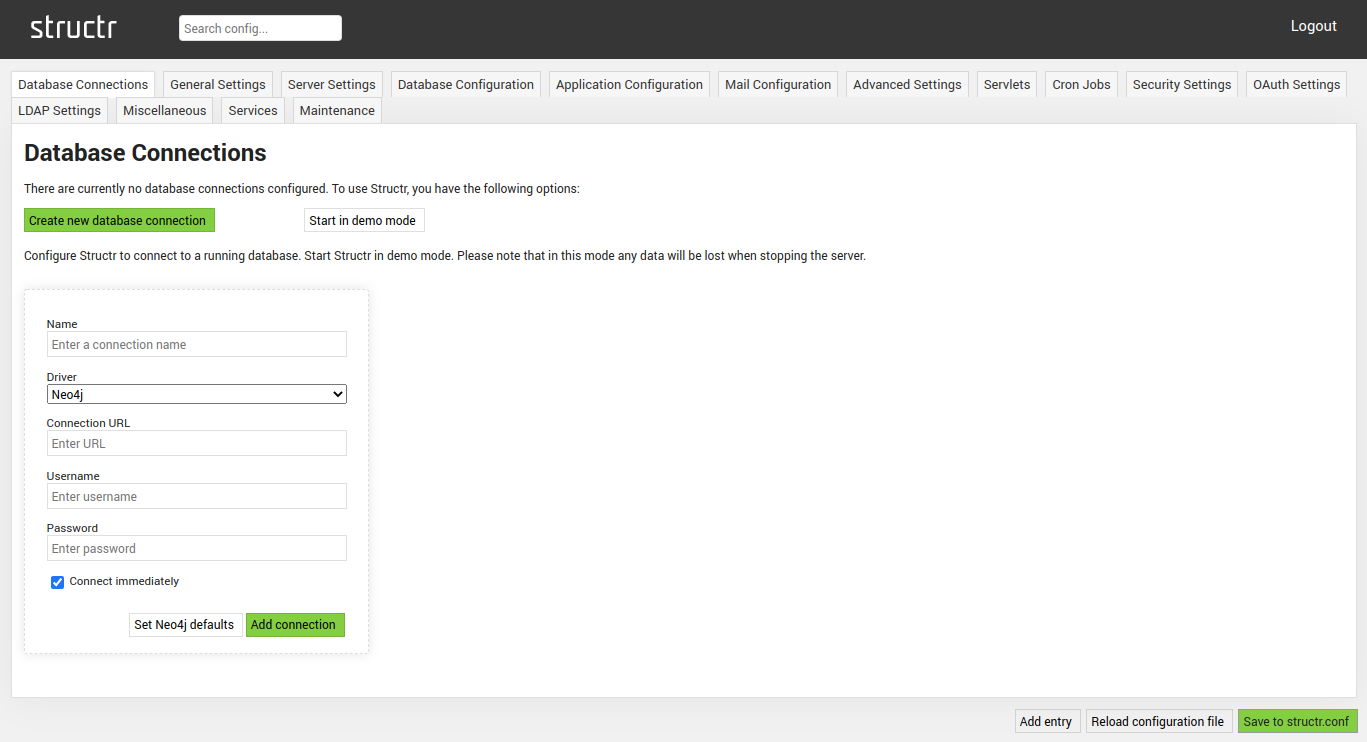
Database Connections
The Database Connections settings allows you to configure the database(s) Structr connects to. Currently three different connection types are supported. Structr can connect either to a Neo4j or Memgraph database.
Note that the Memgraph driver is currently in an experimental stage and may not support the entire feature set of Structr.
Additionally, Structr can run using a so-called in-memory driver, where the database is stored in volatile memory and is whiped when Structr stops. This setting can be useful to quickly start a Structr instance to test some features. A database connection to a neo4j or memgraph database is established using the Create new database connection button ( ); similarly a connection to an in-memory instance is established using the Start in demo mode button (
); similarly a connection to an in-memory instance is established using the Start in demo mode button ( ).
).
For the in-memory database connection no further settings have to be configured, as that database lives entirely inside the RAM and is managed by Structr itself. In contrast, a connection to Neo4j or Memgraph DB requires additional information as detailed below:
| Name | The name of this connection, to allow you to easily distinguish multiple configured connections. |
| Driver | Database driver, either Neo4j or Memgraph DB. |
| Connection URL | URL to the remote database. |
| Database Name | Database name to use (available from v4.1). Defaults to neo4j (if the installation start with an earlier version of neo4j, graph.db will be the correct value) |
| Username | Username to login to the database. |
| Password | Password to login to the database. |
| Connect immediately | Controlls if a connection should be established immediately or manually. |
General Settings
The General Settings tab contains parameters controlling the general behavior of the Structr application, such as indexing and logging. These settings are again subdivided into:
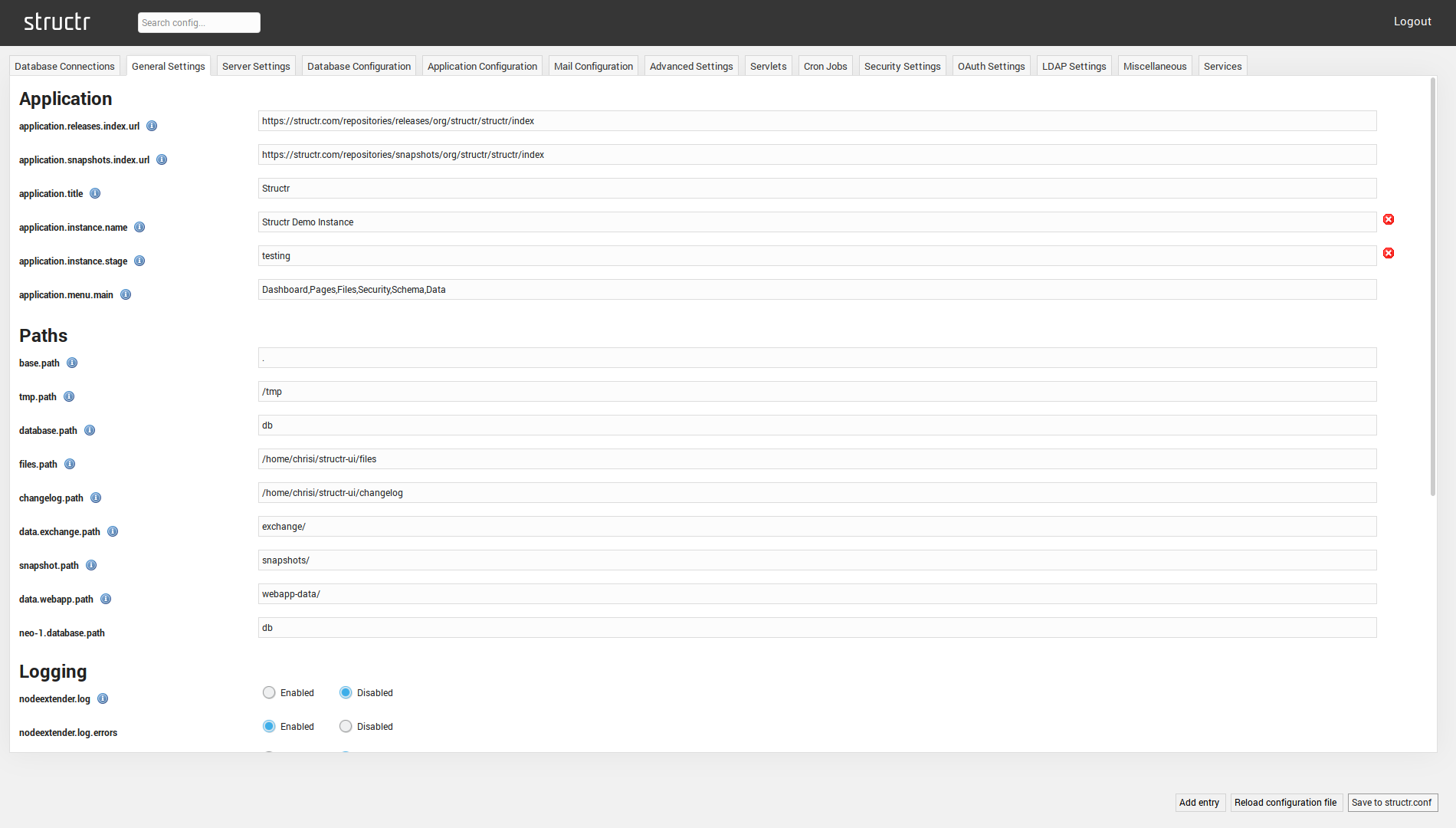
Application
| application.releases.index.url | Contains a URL that is used by the Structr UI to determine the list of available releases to show on the dashboard. |
| application.snapshots.index.url | Contains a URL that is used by the Structr UI to determine the list of available snapshots to show on the dashboard. |
| application.title | The title of the application as shown in the log file. This entry exists for historical reasons and has no functional impact other than appearing in the log file. |
| application.instance.name | The name of this application. In this setting, you can set a string that will be show in the top right corner of the Structr UI. |
| application.instance.stage | The “stage” of the application. In this setting, you can set a string that will be show in the top right corner of the Structr UI together with the instance name. |
| application.menu.main | This setting controls the order and visibility of elements of the Structr main menu. |
| application.console.cypher.maxresults | The maximum number of results returned by a cypher query in the admin console. If a query yields more results, an error message is shown. |
| application.systeminfo.disabled | Disables transmission of telemetry information. This information is used to improve the software and to better adapt to different hardware configurations. |
| application.legacy.requestparameters.enabled | Enables pre-4.0 request parameter names (sort, page, pageSize, etc. instead of _sort, _page, _pageSize, …) |
Warning: The application.menu.main setting is deprecated as of versions 3.5. The usage of the UI Settings tab on the dashboard is encouraged instead.
Paths
| base.path | Path of the Structr working directory. All files will be located relative to this directory. |
| tmp.path | Path to the temporary directory. Uses java.io.tmpdir by default. |
| database.path | Path of the Neo4j db/ directory. |
| files.path | Path to the Structr file storage folder. |
| changelog.path | Path to the Structr changelog storage folder. |
| data.exchange.path | Path to the exchange directory. This path is relative to the base path of the Structr installation to prevent access to files outside of the installation directory. The exchange directory is used by the I/O built-in functions read, write and append. |
| snapshot.path | Path to the snapshot directory. This path is relative to the base path of the Structr installation to prevent access to files outside of the installation directory. The snapshot directory is used by the snapshot() built-in function that allows you to read / write the schema of your application from / to a JSON file. |
| data.webapp.path | Path to the webapp directory. This path is relative to the base path of the Structr installation to prevent access to files outside of the installation directory. The webapp directory is used by the internal web server to serve resource files needed by the Structr UI. |
Logging
| nodeextender.log | Enables the logging of generated Java code of the dynamic schema entities to the logfile. This setting allows you to investigate and debug the generation of Java code for your schema entities in cases where something goes wrong. |
| nodeextender.log.errors | Enables the logging of Java compilation errors when compiling the dynamic schema of your application. |
| log.requests | Enables full request logging for all requests handled by Structr. Caution, the log file can get very large when a lot of requests with lots of content are made. |
| log.functions.stacktrace | Enables stacktrace logging for script calls and built-in functions. If enabled, a scripting error will write the full Java stack trace to the logfile. |
| log.scriptprocess.commandline | Configures the default logging behaviour for the command line generated for script processes. This applies to the exec()- and exec_binary() functions, as well as some processes handling media conversion or processing. For the exec() and exec_binary() function, this can be overridden for each call of the function. Supported values are 0 (Do not log), 1 (Log only script name/path) or 2 (Log script name/path and parameters) |
| log.prefix | Sets the prefix for the request log file that is written when log.requests is enabled. |
| log.javascript.exception.request | Adds path, queryString and parameterMap to JavaScript exceptions (if available) if enabled. |
| log.directorywatchservice.scanquietly | Prevents logging of each scan process for every folder processed by the directory watch service. |
Services
| configured.services | Controls the availability of services in the Structr Services Layer. Only services that are enabled in this setting can be started. |
| services.start.timeout | The number of seconds Structr waits before trying again to start a failed service. |
| services.start.retries | The number of times Structr tries to start a service before it gives up. |
| nodeservice.start.timeout | The number of seconds Structr waits before trying again to start the NodeService. The Node Service is a vital service that provides access to the configured database. |
| nodeservice.start.retries | The number of times Structr tries to start the NodeService before exiting. |
Note: If a vital service cannot be started even after retrying several times, Structr will exit. The configuration key services.start.retries controls this number of retries.
Server Settings
The Server Settings tab contains settings that are related to the various interfaces of a Structr instance.
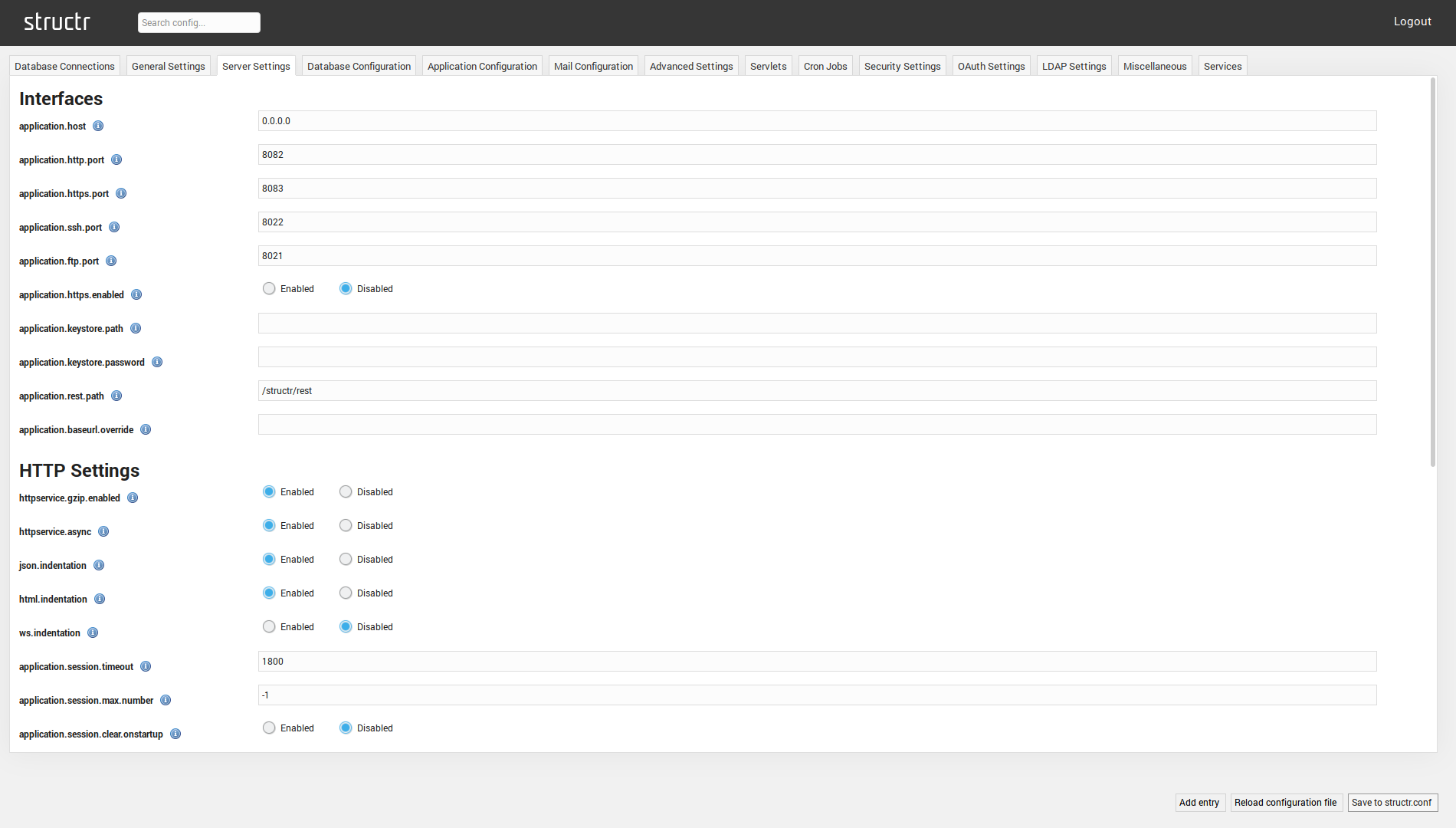
Interfaces
| application.host | The listen address of the Structr HTTP server. If you set the listen address to 127.0.0.1, Structr will only be accessible for applications that run on the local host. This value essentially binds the HTTP server to the local loopback interface. The other option is 0.0.0.0 which makes Structr accessible from all networks. |
| application.http.port | The HTTP port that Structr listens on. If you want to be able to access Structr under a simple http:// URL, you need to set this value to 80. |
| application.https.port | The HTTPS port that Structr listens on. If you want to be able to access Structr under a simple https:// URL, you need to set this value to 443. |
| application.ssh.port | The port that the SSHService listens on. |
| application.ftp.port | The port that the FTPService listens on. |
| application.https.enabled | If enabled, the internal HTTP server will be configured to allow HTTPS connections to the application.https.port. |
| application.keystore.path | The path to a JKS keystore file that contains the certificate chain and private key for the SSL configuration needed for HTTPS. The keystore must be in PCK12 format. |
| application.keystore.password | The password for the JKS keystore used in application.keystore.path. |
| application.baseurl.override | Overrides baseUrl value that is originally assembled dynamically from the protocol, hostname and port of the server instance Structr is running on. |
Note: When configuring the application.http.port to 80, many systems need elevated privileges to bind an application to port 80.
Maintenance
| maintenance.application.http.port | HTTP port the Structr server will listen on in maintenance mode. |
| maintenance.application.https.port | HTTPS port the Structr server will listen on in maintenance mode. |
| maintenance.application.ssh.port | SSH port the Structr server will listen on in maintenance mode. |
| maintenance.application.ftp.port | FTP port the Structr server will listen on in maintenance mode. |
| maintenance.resource.path | The local folder for static resources served in maintenance mode. If no path is provided, a default maintenance page with customizable text is shown in maintenance mode. |
| maintenance.message | Text for default maintenance page. |
HTTP Settings
| httpservice.gzip.enabled | Enables GZIP compression for HTTP transfers. |
| httpservice.async | Enables asynchronous request handling for the HttpService. Disable this option, if you encounter problems with HTTP responses. |
| httpservice.sni.required | Enables strict SNI enforcement for the HttpService. |
| httpservice.sni.hostcheck | Enables SNI host check. |
| json.indentation | Whether JSON ouput should be indented (beautified) or compacted. |
| html.indentation | Whether the page source should be indented (beautified) or compacted. Note: Does not work for template/content nodes which contain raw HTML. |
| ws.indentation | Whether websocket responses should be beautified. |
| application.session.timeout | The session timeout in seconds for HTTP sessions. |
| application.session.max.number | Maximum number of session per user. Defaults to -1 (unlimited). |
| application.session.clear.onstartup | If set to true, all sessions will be cleared during startup. |
| application.session.clear.onshutdown | If set to true, all sessions will be cleared during shutdown. |
HTTPS Settings
| httpservice.force.https | Tries to force HTTPS, if HTTPS is configured and enabled. |
| httpservice.cookies.httponly | Set HttpOnly to true for cookies. |
| httpservice.log.jetty.startupconfig | Prints jetty configuration to log on startup, if enabled. |
| httpservice.ssl.protocols.excluded | Prohibits use of specified protocols. |
| httpservice.ssl.protocols.included | Allows use of specified protocols. |
| httpservice.ssl.ciphers.excluded | Excludes listed ciphers from use. |
CORS Settings
| access.control.accepted.origins | Accepts a comma-seperated list of allowed Origin values. |
| access.control.max.age | Provides a value in seconds for the Access-Control-Max-Age header. |
| access.control.allow.method | Accepts a comma-separated list of allowed HTTP request methods for the Access-Control-Allow-Methods header. |
| allow.control.allow.headers | Accepts a comma-seperated list of allowed headers. Used for Access-Control-Allow-Headers header. |
| access.control.allow.credentials | Accepts a value for the Access-Control-Allow-Credentials header. |
| access.control.expose.headers | Accepts values for the Access-Control-Expose-Headers header. |
Database Configuration
The Database Configuration Settings tab contains settings related to the established database connections of a Structr instance. In contrast to the Database Connections Settings, the Database Configuration Settings control properties of the database connection itself, such as caching, debugging, synchronization and result sizes. This section is divided into the following subsections:
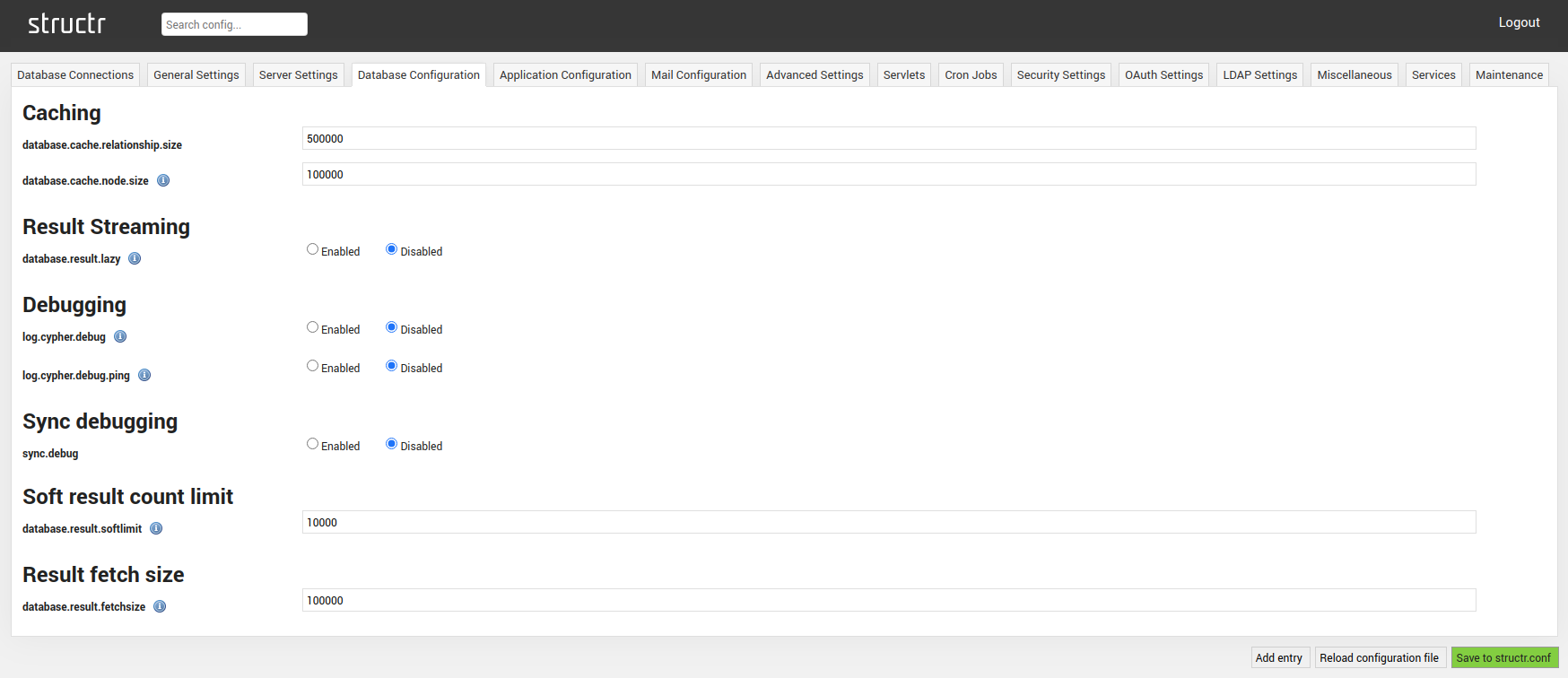
Caching
| database.cache.relationship.size | Specifies the relationship cache size. |
| database.cache.node.size | Specifies the node cache size. |
Result Streaming
| database.result.lazy | Forces Structr to use lazy evaluation for relationship queries. |
Debugging
| log.cypher.debug | Prints all generated cypher queries to the server log. if enabled. |
| log.cypher.debug.ping | If enabled, queries generated for the Websocket PING request will be logged. Can only be used in conjunction with log.cypher.debug. |
Soft result count limit
| database.result.softlimit | Applies a soft limit on the result size of queries. If queries exceed the specified number of results, it will not display the exact result count, but the soft limit instead. |
Result fetch size
| database.result.fetchsize | Number of records fetched per batch when fetching large results. |
Application Configuration
The Application Configuration Settings tab contains all settings controlling the behavior of the running application. In particular this includes settings regarding the Filesystem and Schema, as well as Encryption, Login behavior and Application Security. The Application Configuration Settings are subdivided into the following sections:
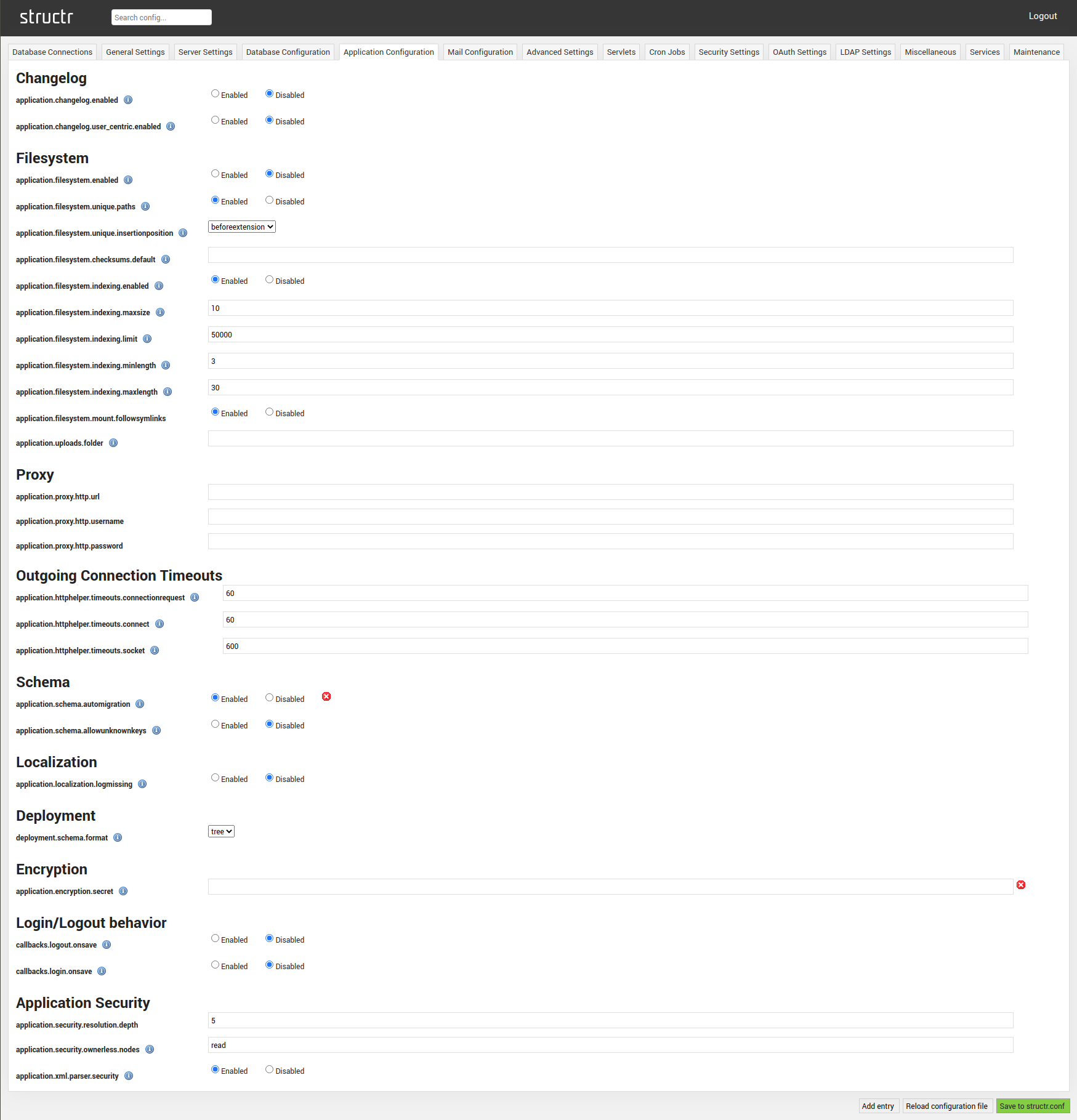
Changelog
| application.changelog.enabled | If enabled, all changes to nodes and relationships will be written to a changelog. |
| application.changelog.user_centric.enabled | Enables a special kind of changelog, which logs user activities. |
Filesystem
| application.filesystem.enabled | Enables the creation of home directories for each users. |
| application.filesystem.unique.paths | Enforces unique paths for files and folders. |
| application.filesystem.unique.insertionposition | | start | prefixes the name with a timestamp | | beforeextension | puts the timestamp before the last dot (or at the end if the name does not contain a dot) | | end | appends the timestamp after the complete name |
|
| application.filesystem.checksums.default | List of checksums to be calculated on file creation by default. |
| application.filesystem.indexing.enabled | Globally enables indexing. Indexing can still be controlled on a file basis. |
| application.filesystem.indexing.maxsize | Maximum size (MB) for a file to be indexed. |
| application.filesystem.limit | Maximum number of words to be indexed per file. |
| application.filesystem.indexing.minlength | Minimum length of words to be indexed. |
| application.filesystem.indexing.maxlength | Maximum length of words to be indexed. |
| application.filesystem.mount.followsymlinks | Enables support for symbolic links in mounted directories. |
| applications.uploads.folder | Default path for files uploaded via the UploadServlet. |
Proxy
| application.proxy.http.url | Specifies the proxy url for built-in HTTP function calls. |
| application.proxy.http.username | Specifies the proxy username for built-in HTTP function calls. |
| application.proxy.http.password | Specifies the proxy password for built-in HTTP function calls. |
Outgoing Connection Timeouts
| applications.httphelper.timeouts.connectionrequests | Specifies a timeout for the request of an outgoing HTTP connection from the connection manager in seconds. A zero value is interpreted as infinite. |
| application.httphelper.timeouts.connect | Specifies a timeout in seconds until an outgoing HTTP connection is established. A zero value is interpreted as infinite. |
| application.httphelper.timeouts.socket | Specifies a timeout for the HTTP socket. If the time between two consecutive data packets is greater than the specified value, a timeout occurs. A zero value is interpreted as infinite. |
Schema
| application.schema.automigration | Allows Structr to attempt an automatic migration of the schema between different Structr versions. |
| application.schema.allowunknownkeys | Allows access to properties that are not specified in the schema via get/set-Operations. |
Localization
| application.localization.logmissing | If enabled, missing requested localizations are logged. |
| application.localization.usefallbacklocale | Turns on usage of fallback locale if for the current locale no localization is found |
| application.localization.fallbacklocale | The default locale used, if no localization is found and using a fallback is active. |
Deployment
| deployment.schema.format | Specifies the deployment format. Valid values are “file” and “tree”. Preferrably set to “tree” as “file” is the legacy deployment format. |
Encryption
| application.encryption.secret | Sets the global secret used to encrypt string properties. Using this configuration setting is one of several possible ways to set the secret, and it is not recommended for production environments because the key can easily be read by an attacker with scripting access. |
Login/Logout Behaviour
| callbacks.logout.onsave | When set to true a user logout will trigger the onSave method on the user. Disabled by default as the global handler onStructrLogout can be used to achieve similar results. |
| callbacks.login.onsave | When set to true a user login will trigger the onSave method on the user. Disabled by default as the global handler onStructrLogin can be used to achieve similar results. Triggers on failed login attempts and on each step of the two-factor authentication process. |
Application Security
| application.security.resolution.depth | Maximum number of nodes that are traversed for security resolution. |
| application.security.ownerless.nodes | The user permission level on ownerless nodes. One or more of: read, write, delete, accessControl |
| application.xml.parser.security | Enables various measures to prevent XML parsing exploits. |
Mail Configuration
The Mail Configuration Settings tab contains all settings controlling the behavior of the mail service. It is subdivided into the following sections:
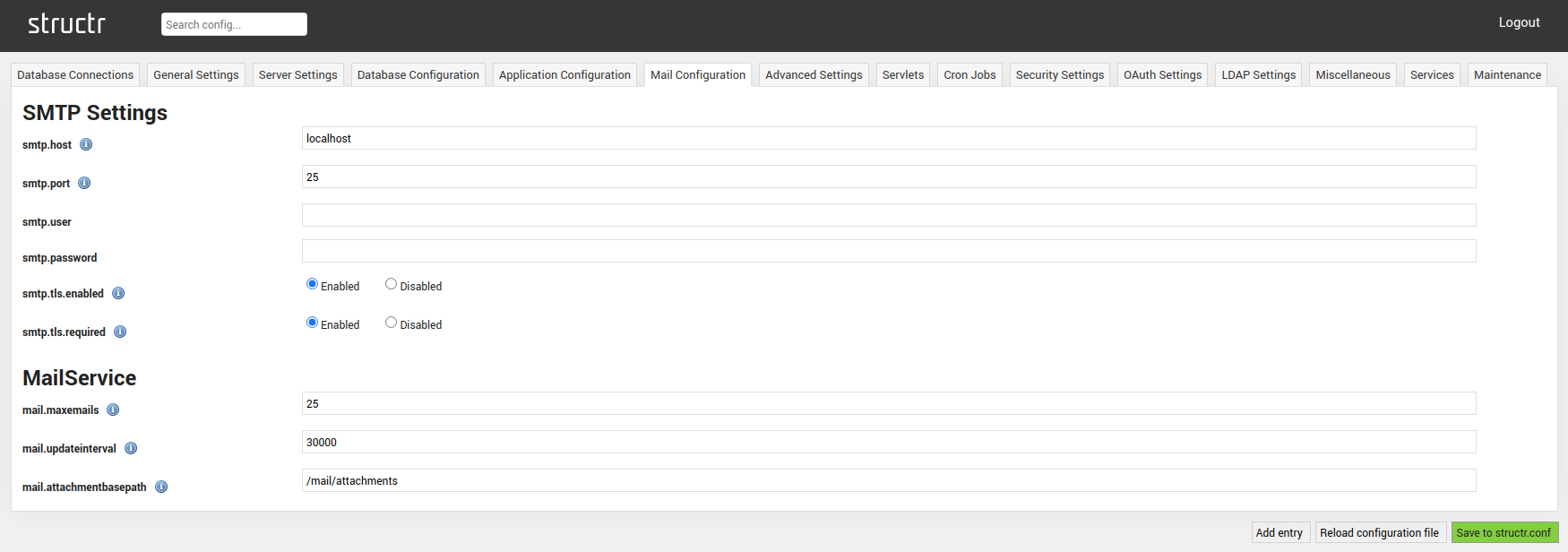
SMTP Settings
| smtp.host | Address of the mail server used for SMTP. |
| smtp.port | Port of the SMTP server. |
| smtp.user | Username for the SMTP server. |
| smtp.password | Password for the SMTP server. |
| smtp.tls.enabled | Enables TLS for the SMTP connection. |
| smtp.tls.required | Forces TLS for the SMTP connection. |
MailService
| mail.maxemails | Maximum amount of emails that are synchronized for each mail account. |
| max.updateinterval | Interval in milliseconds at which mailboxes are checked. |
| max.attachmentbasepath | Base path in the filesystem for the storage of mail attachments. |
Advanced Settings
The Advanced Settings tab contains settings controlling specialized aspects of a Structr application, such as Geocoding. It is subdivided into the following sections:
JSON
| json.parrallelization.threshold | Collection size threshold for multi-threaded JSON generation. |
| json.lenient | Whether to use lenient serialization, e.g. allow to serialize NaN, -Infinity, Infinity instead of just returning null. Node: as long as Javascript doesn’t support NaN etc, most of the UI will be broken. |
| json.output.forcearrays | Forces collections with a single element to always be represented as a proper collection. |
Geocoding
| geocoding.provider | Fully qualified class name of the geocoding provider. |
| geocoding.language | Locale for the geocoding functionality. |
| geocoding.apikey | API key for the geocoding provider. |
| dateproperty.defaultformat | Default format for all date properties. Defaults to ISO8601 pattern. |
Servlets
The Servlets Settings tab contains settings controlling the properties of the individual servlets in Structr. It is subdivided into the following subsections:
General
| httpservice.servlets | Enables specified servlets. Can be configured via UI or by specifying a space-seperated list of servlet names in die configuration file. |
ConfigServlet
JsonRestServlet
| jsonrestservlet.defaultview | Default view to use when no view is given in the URL. |
| jsonrestservlet.outputdepth | Maximum nesting depth of JSON output. |
| jsonrestservlet.user.class | User class that is instantiated when new users are created via the servlet. |
| jsonrestservlet.user.autologin | Only works in conjunction with the jsonrestservlet.user.autocreate key. Will log in user after self registration. |
| jsonrestservlet.user.autocreate | Enable this to support user self registration. |
FlowServlet
| flowservlet.defaultview | Default view to use when no view is given in the URL. |
| flowservlet.outputdepth | Maximum nesting depth of JSON output. |
HtmlServlet
| htmlservlet.defaultview | Default view to use when no view is given in the URL. |
| htmlservlet.outputdepth | Maximum nesting depth of JSON output. |
| htmlservlet.resolveproperties | Specifies the list of properties that are be used to resolve entities from URL paths. |
| htmlservlet.customresponseheaders | List of custom response headers that will be added to every HTTP response. |
PdfServlet
| pdfservlet.defaultview | Default view to use when no view is given in the URL. |
| pdfservlet.outputdepth | Maximum nesting depth of JSON output. |
| pdfservlet.resolveproperties | Specifies the list of properties that are be used to resolve entities from URL paths. |
| pdfservlet.customresponseheaders | List of custom response headers that will be added to every HTTP response. |
WebsocketServlet
| websocketservlet.outputdepth | Maximum nesting depth of JSON output. |
CsvServlet
| csvservlet.defaultview | Default view to use when no view is given in the URL. |
| csvservlet.outputdepth | Maximum nesting depth of JSON output. |
UploadServlet
| uploadservlet.allowanonymousuploads | Allows anonymous users to upload files. |
| uploadservlet.maxfilesize | Maximum allowed file size for single file uploads. Unit is Megabytes |
| uploadservlet.maxrequestsize | Maximum allowed request size for single file uploads. Unit is Megabytes |
GraphQLServlet
| graphqlservlet.defaultview | Default view to use when no view is given in the URL. |
| graphqlservlet.outputdepth | Maximum nesting depth of JSON output. |
LoginServlet
| loginservlet.defaultview | Default view to use when no view is given in the URL. |
| loginservlet.outputdepth | Maximum nesting depth of JSON output. |
LogoutServlet
| logoutservlet.defaultview | Default view to use when no view is given in the URL. |
| logoutservlet.outputdepth | Maximum nesting depth of JSON output. |
DeploymentServlet
| deploymentservlet.allowanonymousdeployments | Allow anonymous users to trigger a deployment process. |
| deploymentservlet.allowanonymousuploads | Allow anonymous users to upload deployment files. |
| deploymentservlet.maxfilesize | Maximum allowed file size for single file uploads. Unit is Megabytes. |
| deploymentservlet.maxrequestsize | Maximum allowed request size for single file uploads. Unit is Megabytes. |
HealthCheckServlet
| healthcheckservlet.whitelist | IP addresses in this list are allowed to access the health check endpoint at /structr/health. |
Cron Jobs
The Cron Jobs Settings tab contains settings to create new cron jobs, as well as setting controlling all existing cron jobs. New cron jobs can be configured via the following configuration keys:
| cronservice.tasks | List of comma-seperated fully qualified names of classes implementing Task or names of global schema methods that will be called. |
| cronservice.allowparallelexecution | Allows the same cron job to run more than once. This can happen, if the execution of a cron task takes longer than it’s trigger interval. |
Custom
The custom section contains a list of all configured cronservice.tasks, where the key <taskName>.cronExpression controlls in which time interval the cron expression is to be executed. So for the example above, the cronservice task updateStatus will generate the key updateStatus.cronExpression.
<taskName>.cronExpression | Expression controlling the time intervals at which the cron task is to be scheduled. |
The cronExpression in Structr can be configured as <taskName>.cronExpression = <s> <m> <h> <dom> <M> <dow>. Structr will then run the specified tasks with the configured frequency as the admin user.
| Field | Explanation | Value Range |
|---|
<s> | seconds of the minute | 0-59 |
<m> | minute of the hour | 0-59 |
<h> | hour of the day | 0-23 |
<dom> | day of the month | 0-31 |
<m> | month of the year | 1-12 |
<dow> | day of the week | 0-6 (0 = Sunday) |
For more information see this article:
Security Settings
The Security Settings tab contains all settings controlling the security properties of a Structr application. In particular they include properties such as two factor authentication, password policies and let’s encrypt configurations. The Security Settings are subdivided into the following subsections:
Superuser
| superuser.name | Name of the super user account. |
| superuser.password | Password of the super user account. |
Two Factor Authentification
| security.twofactorauthentification.level | Sets whether 2FA is enabled, optional or disabled. Valid values are: forced, optional, off |
| security.twofactorauthentification.issuer | Name of the 2FA issuer. Must be URL-compliant in order to generate valid QR codes. |
| security.twofactorauthentification.algorithm | Respected by the most recent Google Authenticator implementations. |
| security.twofactorauthentification.digits | Amount of digits in the 2FA code. |
| security.twofactorauthentification.period | Defines the period that a TOTP code will be valid for, in seconds. Respected by the most recent Google Authenticator implementations. |
| security.twofactorauthentification.logintimeout | Defines how long the two-factor login time window in seconds is. After entering the username and password the user has this amount of time to enter a two factor token before he has to re-authenticate via password. |
| security.twofactorauthentification.loginpage | The application page where the user enters the current two factor token. |
| security.twofactorauthentification.whitelistedips | A comma-separated (,) list of IPs for which two factor authentication is disabled. Both IPv4 and IPv6 are supported. CIDR notation is also supported. For example: 192.168.0.1/24 would whitelist 192.168.0.1 - 192.168.0.254 |
JWT Auth
| security.jwt.secrettype | Selects the secret type that will be used to sign or verify a given access or refresh token. |
| security.jwt.secret | Used if ‘security.jwt.secrettype’=secret. The secret that will be used to sign and verify all tokens issued and sent to Structr. Must have a min. length of 32 characters. |
| security.jwt.jwtissuer | The issuer for the JWTs created by this Structr instance. |
| security.jwt.expirationtime | Access token timeout in minutes. |
| security.jwt.refreshtoken.expirationtime | Refresh token timeout in minutes. |
| security.jwt.keystore | Used if ‘security.jwt.secrettype’=keypair. A valid keystore file containing a private/public keypair that can be used to sign and verify JWTs |
| security.jwt.keystore.password | The password for the given ‘security.jwt.keystore’. |
| security.jwt.key.alias | The alias of the private key of the given ‘security.jwt.keystore’. |
| security.jwks.provider | The URL of the authentication system that issues JWTs. Structr will try to read the .well-known information of the service. |
Password Policy
| security.passwordpolicy.forcechange | Indicates if a forced password change is active. |
| security.passwordpolicy.onchange.clearsessions | Clear all sessions of a user on password change. |
| security.passwordpolicy.maxage | The number of days after which a user has to change his password. |
| security.passwordpolicy.remindtime | The number of days (before the user must change the password) where a warning should be issued. (Has to be handled in application code). |
| security.passwordpolicy.maxfailedattempts | The maximum number of failed login attempts before a user is blocked. (Can be disabled by setting to zero or a negative number). |
| security.passwordpolicy.restfailedattemptspasswordreset | Configures if resetting the users password also resets the failed login attempts counter. |
SSH
| application.ssh.forcepublickey | Force use of public key authentication for SSH connections. |
User Self Registration
| jsonrestservlet.user.autocreate | Enable this to support user self registration. |
| registration.customuserclass | Specifies a special user class to be used when creating new users. |
| registration.allowloginbeforeconfirmation | Enables self-registered users to login without clicking the activation link in the registration email. |
| registration.customeruserattributes | Attributes the registering user is allowed to provide. All other attributes are discarded. (eMail is always allowed. It will always be included, so removing it here has no effect. It’s a generally a bad idea to include security-relevant attributes here as they can be set from an unauthenticated, unauthorized source. If unsure or you don’t know what that means, set only eMail.) |
Confirmation Key Validity
| confirmationkey.passwordreset.validityperiod | Validity period (in minutes) of the confirmation key generated when a user resets his password. Default is 30. |
| confirmationkey.registration.validityperiod | Validity period (in minutes) of the confirmation key generated during self registration. Default is 2 days (2880 minutes). |
| confirmationkey.validwithouttimestamp | How to interpret confirmation keys without a timestamp. |
Let's Encrypt
| letsencrypt.wait | Wait for this amount of seconds before trying to authorize challenge. Default is 300 seconds (5 minutes). |
| letsencrypt.challenge.type | Challenge type for Let’s Encrypt authorization. Possible values are ‘http’ and ‘dns’. |
| letsencrypt.domains | Space-separated list of domains to fetch and update Let’s Encrypt certificates for. |
| letsencrypt.production.server.url | URL of Let’s Encrypt server. Default is ‘acme://letsencrypt.org’. |
| letsencrypt.staging.server.url | URL of Let’s Encrypt staging server for testing only. Default is ‘acme://letsencrypt.org/staging’. |
| letsencrypt.user.key.filename | File name of the Let’s Encrypt user key. Default is ‘user.key’. |
| letsencrypt.domain.key.filename | File name of the Let’s Encrypt domain key. Default is ‘domain.key’. |
| letsencryt.domain.csr.filename | File name of the Let’s Encrypt CSR. Default is ‘domain.csr’. |
| letsencrypt.domain.chain.filename | File name of the Let’s Encrypt domain chain. Default is ‘domain-chain.crt’. |
| letsencrypt.key.size | Encryption key length. Default is 2048. |
OAuth Settings
The OAuth Settings tab contains all configuration keys controlling the OAuth setup of the running Structr instance. In particular, Structr supports GitHub, Twitter, LinkedIn, Google and Facebook. The OAuth Settings tab is divided into the following subsections:
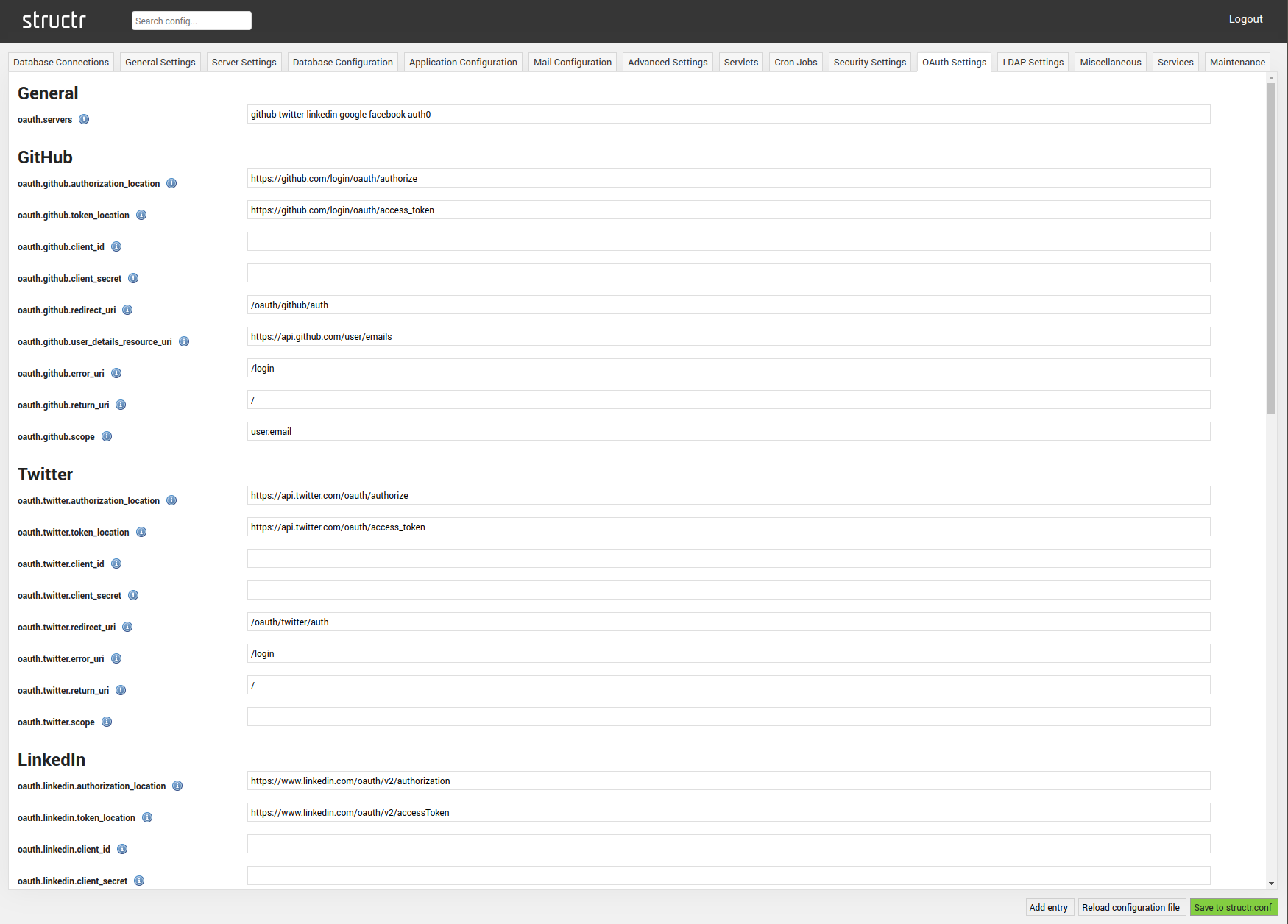
General
| oauth.servers | Space-seperated List of available oauth services. Defaults to “github twitter linkedin google facebook auth0”. |
Github
| oauth.github.authorization_location | URL of the authorization endpoint. |
| oauth.github.token_location | URL of the token endpoint. |
| oauth.github.client_id | Client ID used for oauth. |
| oauth.github.client_secret | Client secret used for oauth. |
| oauth.github.redirect_uri | Structr endpoint for the service oauth authorization. |
| oauth.github.user_details_resource_uri | Points to the user details endpoint of the service provider. |
| oauth.github.error_uri | Structr redirects to this URI on unsuccessful authentication. |
| oauth.github.return_uri | Structr redirects to this URI on successful authentification. |
| oauth.github.scope | Specifies the scope of the authentifcation. |
| oauth.twitter.authorization_location | URL of the authorization endpoint. |
| oauth.twitter.token_location | URL of the token endpoint. |
| oauth.twitter.client_id | Client ID used for oauth. |
| oauth.twitter.client_secret | Client secret used for oauth. |
| oauth.twitter.redirect_uri | Structr endpoint for the service oauth authorization. |
| oauth.twitter.error_uri | Structr redirects to this URI on unsuccessful authentication. |
| oauth.twitter.return_uri | Structr redirects to this URI on successful authentification. |
| oauth.twitter.scope | Specifies the scope of the authentifcation. |
LinkedIn
| oauth.linkedin.authorization_location | URL of the authorization endpoint. |
| oauth.linkedin.token_location | URL of the token endpoint. |
| oauth.linkedin.client_id | Client ID used for oauth. |
| oauth.linkedin.client_secret | Client secret used for oauth. |
| oauth.linkedin.redirect_uri | Structr endpoint for the service oauth authorization. |
| oauth.linkedin.user_details_resource_uri | Points to the user details endpoint of the service provider. |
| oauth.linkedin.user_profile_resource_uri | Points to the user profile endpoint of the service provider. |
| oauth.linkedin.error_uri | Structr redirects to this URI on unsuccessful authentication. |
| oauth.linkedin.return_uri | Structr redirects to this URI on successful authentification. |
| oauth.linkedin.scope | Specifies the scope of the authentifcation. |
Google
| oauth.google.authorization_location | URL of the authorization endpoint. |
| oauth.google.token_location | URL of the token endpoint. |
| oauth.google.client_id | Client ID used for oauth. |
| oauth.google.client_secret | Client secret used for oauth. |
| oauth.google.redirect_uri | Structr endpoint for the service oauth authorization. |
| oauth.google.user_details_resource_uri | Points to the user details endpoint of the service provider. |
| oauth.google.error_uri | Structr redirects to this URI on unsuccessful authentication. |
| oauth.google.return_uri | Structr redirects to this URI on successful authentification. |
| oauth.google.scope | Specifies the scope of the authentifcation. |
Facebook
| oauth.facebook.authorization_location | URL of the authorization endpoint. |
| oauth.facebook.token_location | URL of the token endpoint. |
| oauth.facebook.client_id | Client ID used for oauth. |
| oauth.facebook.client_secret | Client secret used for oauth. |
| oauth.facebook.redirect_uri | Structr endpoint for the service oauth authorization. |
| oauth.facebook.user_details_resource_uri | Points to the user details endpoint of the service provider. |
| oauth.facebook.error_uri | Structr redirects to this URI on unsuccessful authentication. |
| oauth.facebook.return_uri | Structr redirects to this URI on successful authentification. |
| oauth.facebook.scope | Specifies the scope of the authentifcation. |
Auth0
| oauth.oauth.authorization_location | URL of the authorization endpoint. |
| oauth.oauth.token_location | URL of the token endpoint. |
| oauth.oauth.client_id | Client ID used for oauth. |
| oauth.oauth.client_secret | Client secret used for oauth. |
| oauth.oauth.redirect_uri | Structr endpoint for the service oauth authorization. |
| oauth.oauth.user_details_resource_uri | Points to the user details endpoint of the service provider. |
| oauth.oauth.error_uri | Structr redirects to this URI on unsuccessful authentication. |
| oauth.oauth.return_uri | Structr redirects to this URI on successful authentification. |
| oauth.oauth.scope | Specifies the scope of the authentifcation. |
LDAP Settings
The LDAP Settings tab allows you to configure Structr to establish an LDAP connection.
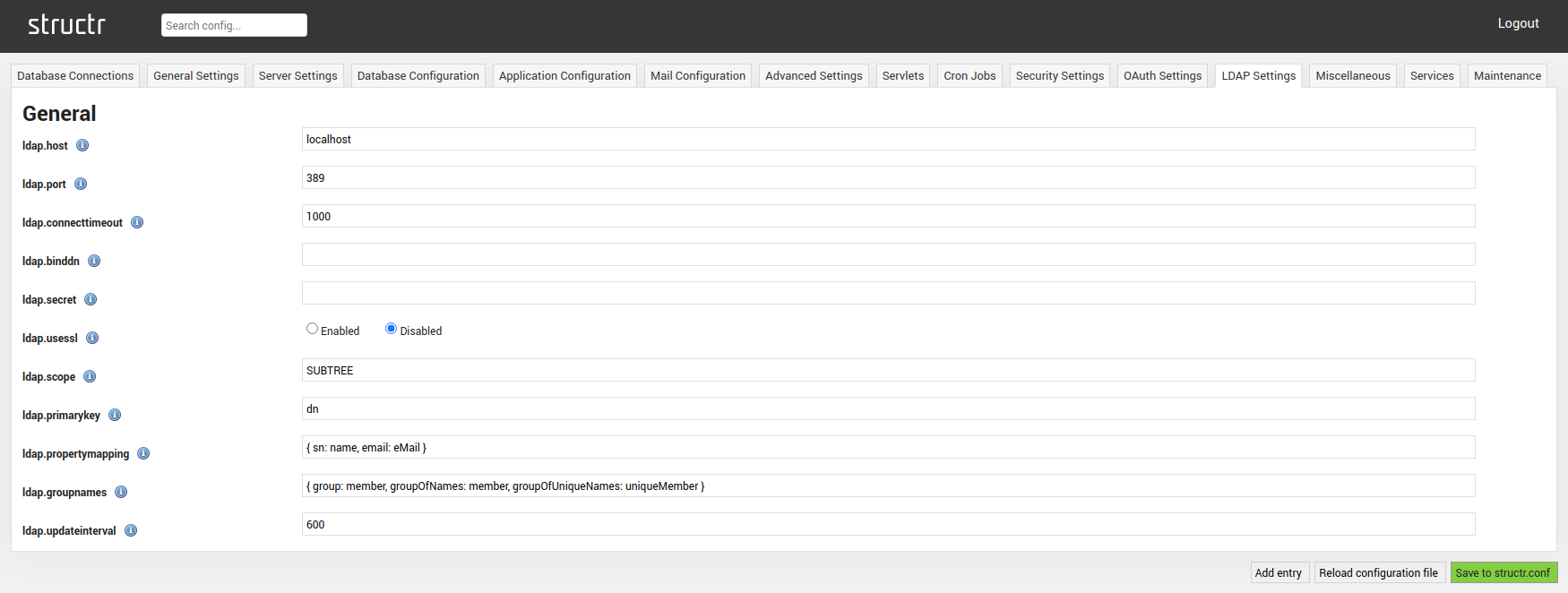
General
| ldap.host | Address of the LDAP host. |
| ldap.port | Port of the LDAP host. |
| ldap.connectiontimeout | Connection timeout in milliseconds. |
| ldap.binddn | DN that is used to authenticate synchronization. |
| ldap.secret | Used in conjunction with bind DN to handle authentication. |
| ldap.usessl | Enables SSL for the LDAP connection. |
| ldap.scope | Specifies the LDAP scope. Defaults to “SUBTREE”. |
| ldap.primarykey | Name of primary identification property of LDAP objects, must uniquely identify users and groups. |
| ldap.propertymapping | Mapping from LDAP properties to Structr properties. |
| ldap.groupnames | LDAP objectclass tuples for group and member identification. |
| ldap.updateinterval | Update interval for group synchronization in seconds. |
Miscellaneous
The Miscellaneous Setting tab contains settings to control payment options via paypal, api keys for the google translation module and other custom settings. It is subdivided into the following sections:

Payment Options
| paypal.mode | Can be set to “sandbox” or “live” for staging or production setups. |
| paypal.username | Sets the PayPal username for the account to be used. |
| paypal.password | Sets the PayPal password for the account to be used. |
| paypal.signature | Sets the PayPal signature for the account to be used. |
| paypal.redirect | Sets the uri to which the PayPal service is redirected. |
| stripe.apikey | Sets the API key for the Stripe service. |
Translation Module
| translation.google.apikey | Sets the API key for Google services. |
| translation.deepl.apikey | Sets the API key for the DeepL service. |
Custom
| cronservice.active |
| nodeservice.active |
| directorywatchservice.active |
| httpservice.active |
| agentservice.active |
| schemaservice.active |
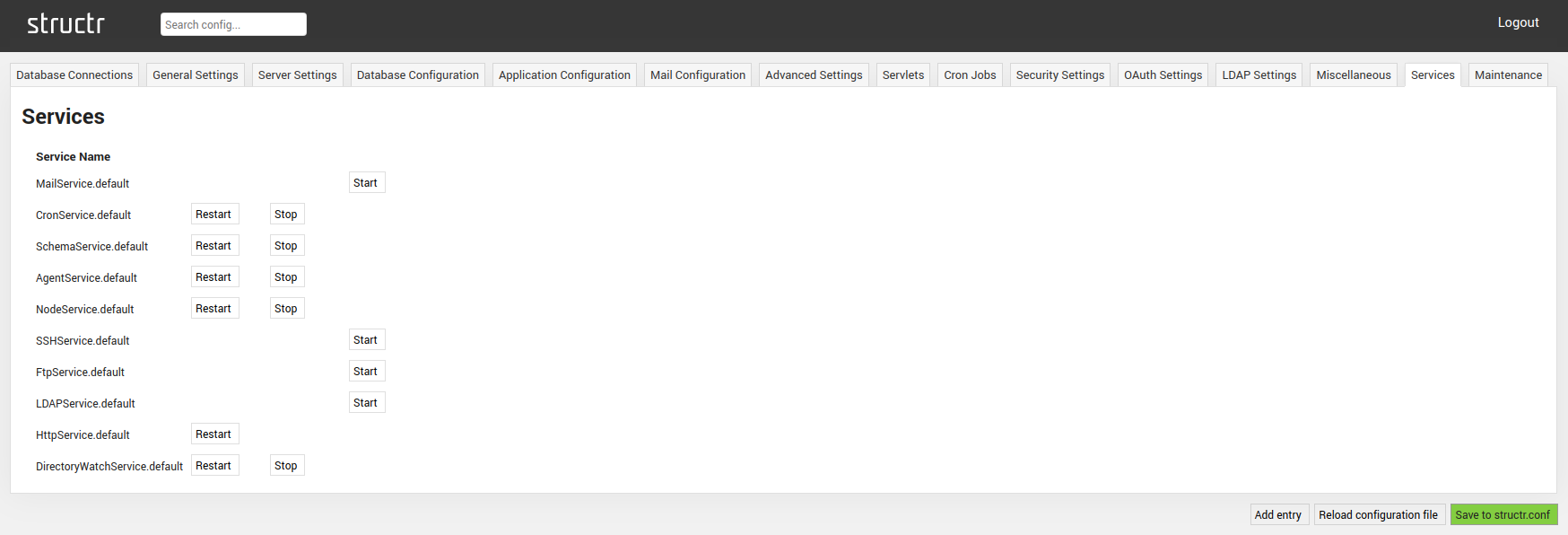
Services
The Services Settings tab allows you to (re)start and stop Structr services. The available services include a MailService, CronService, SchemaService, AgentService, NodeService, SSHService, FtpService, LDAPService, HttpService, as well as a DirectoryWatchService.
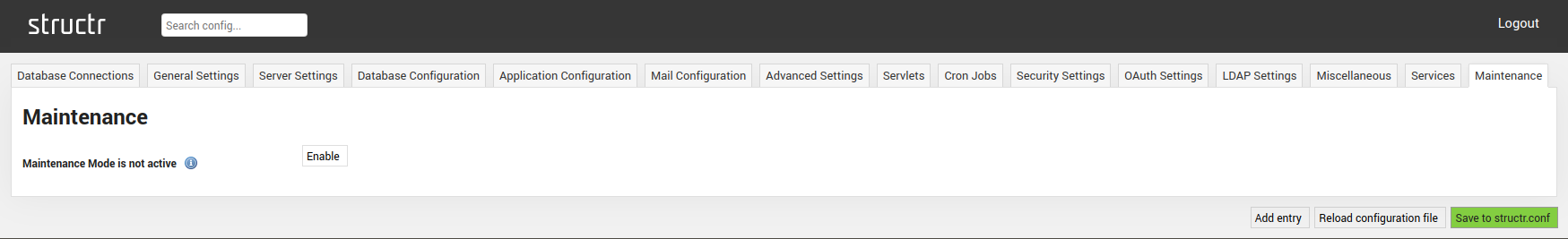
Maintenance
The Maintenance Settings tab allows you to en- or disable the maintenance mode of Structr.
![]() ); similarly a connection to an in-memory instance is established using the Start in demo mode button (
); similarly a connection to an in-memory instance is established using the Start in demo mode button (![]() ).
).













